Get Started; Footprinting and Reconnaissance
Quickly mapping an organisations attack surface is an essential skill for network attackers (penetration testers, bug bounty hunters or Mr Robot) as well as those who are defending the network (network security folks, system administrators, blue teams etc).
A detailed footprint of an organisations Internet facing systems is a tactical resource that can be used by both attackers and defenders. By developing an understanding of the attack surface skilled security analysts are able to quickly identify weak areas in the attack surface.
Discovered assets such as old servers, custom web applications and forgotten services are often the first crumbs in a trail that leads to a compromise.
Attack Surface Discovery is a Time Critical Process
The Blue Team needs to understand the tactics that penetration testers and bug bounty hunters are using to map the attack surface. These tactics will often be also employed by targeted attackers. By quickly identifying weak areas in your attack surface you will enable prioritisation of mitigation to defend those systems and applications.
Penetration Testers need to quickly identify the weak spots so that they can gain access and ensure that the engagement is successful. The nature of a penetration test is time constrained so the faster areas to attack are identified the more likely the test will be a success.
Bug Bounty Hunters need to quickly identify weak spots to find the bugs and get the bounty. Since a hunter is competing against others in the race to find bugs, being faster can often mean getting paid. This is not to say that more involved deeper bug discoveries do not take time to develop, but a quick wins give you time to go for more.
Footprinting a Domain is an Iterative Process
After working through the process of footprinting a domain, you will quickly realise how it is a cyclic process. The output from searching against the domain, provides new inputs into the same domain search process. This can go on for quite some time, with both time and scope factors in the value of continuing the discovery.
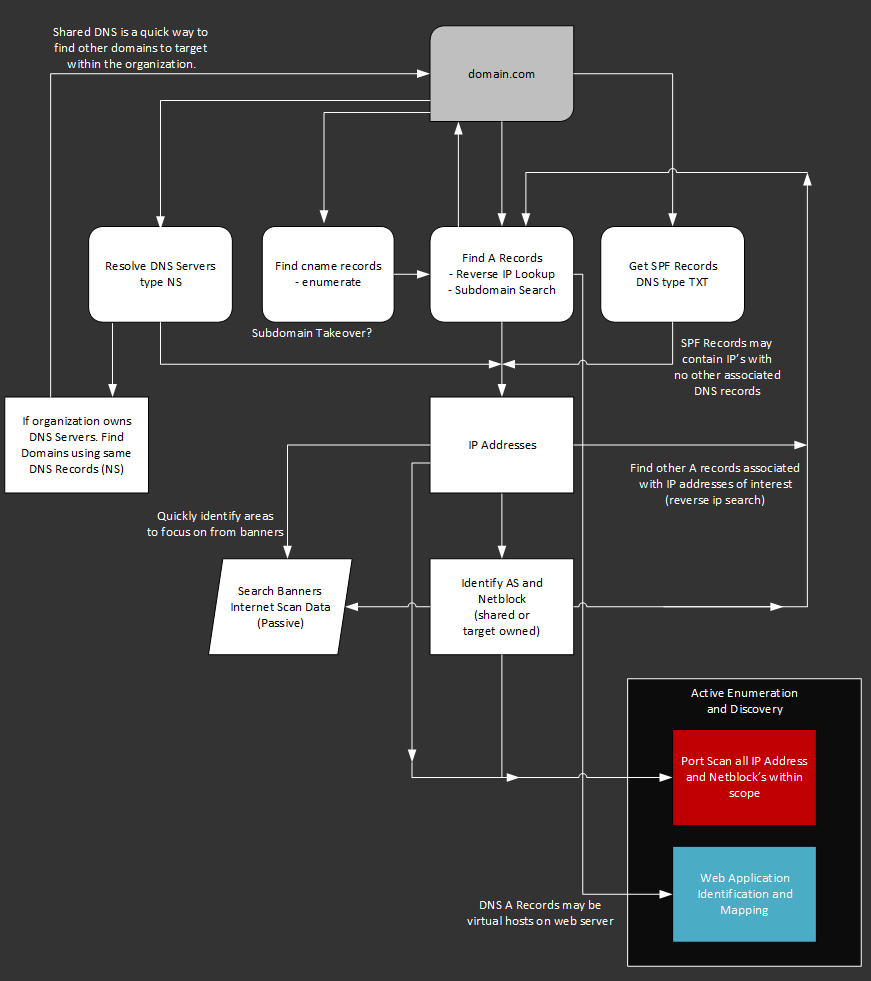
Overview of the Network Discovery Process
Paying Attention to Scope
As you discover assets and networks, pivoting to new areas of interest it is very important that you pay attention to the scope of your engagement. Both penetration tests and bug bounties often have a defined scope. If you start active scanning against areas outside of the scope, you may quickly end up getting into trouble or at the very least appear unprofessional. If you discover things of Interest outside the scope, take note and include your passive findings in the report or consult with the program / engagement contact to see if it could be included.
Secrets of DNSDumpster
The domain search is the most obvious report that users will find useful when utilising DNSDumpster. There are a number of not so obvious features that will rapidly increase the attack surface. Take your reconnaissance from a quick overview to actionable intelligence.
Pivot to Identify Service Banners of a Netblock
Each discovered host has the an option to search the netblock that the host is sitting in for banners that have been discovered through Internet wide scans. Think of this like target focused searches of scans.io, censys or shodan.
Banners are available for the following TCP ports. These have been selected as they are common services, with banners that often reveal operating system and other useful data.
Banner search example
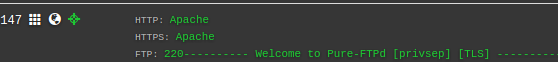
Further discovery will be required further down the assessment process with port scans and other network based scanning. For now the benefit of these banners is a quick overview to identify operating system and server role which can reveal the security posture of the organisation.
The netblock may be a hosted range operated by a third party company where the other hosts within the range are not of interest. However, if the range is operated by the target organisation the banners can reveal additional hosts of interest that are not present in the DNS only reports.
To search for the banners of a network you can simply enter the CIDR notation of the network in the DNSDumpster search field.
Discover Web Sites Present on a Host
A common web hosting feature is the use of virtual hosts. That is hosting multiple web sites on a single web server, using different A records for the sites.
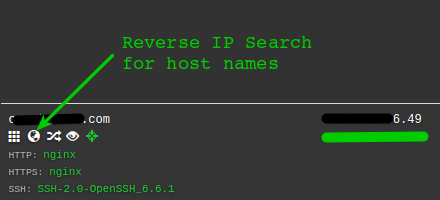
Using the HackerTarget.com Reverse IP Search API the host search button in the record can reveal other web sites hosted on the server. These may have vulnerabilities or weakness that lead to compromise of the underlying host.
Reverse IP Search for other Host Names
Shared DNS Servers
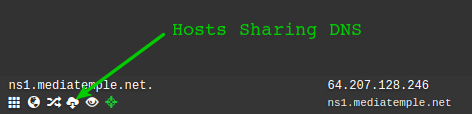
If the organisation hosts its own name servers then the attack surface can be increased significantly by finding all the domains that the organisation is hosting on those name servers.
This can be done by doing a Reverse DNS Name Server search against a DNS data set. For example ns1.exampletarget.com, is the primary server for our organisation. By searching the data set for all NS records that point to ns1.exampletarget.com we reveal all the domains that are configured on this server.
Shared DNS Search example
We can then pivot to search for the newly discovered domains, once again looking for new IP addresses, host names and web sites to assess.
SPF TXT Records
The SPF record is a benefit to anti-spam efforts for an organisation. It basically is a record of IP addresses that are allowed to send email for the domain. This can mean that the SPF record may contain IP addresses for netblocks that are otherwise not found using other DNS reconnaissance.
Perhaps the IP range of the organisations office network. It does not have any services hosted within the netblock, but there is an internal mail server that needs to send email outbound so it is listed in the SPF record or maybe there is a monitoring server that needs to send email notifications.
Wrapping Up
This introduction to footprinting and reconnaissance has barely scratched the surface of the possibilities in OSINT discovery. If you are just getting started; get familiar with these DNS focused enumeration techniques and soak up as much knowledge as you can. It is a great time to get into the field of security testing; start to play with Capture the Flag (CTF's), then try some Bug Bounties and get ready to learn. Persistence and creativity will go a long way.
For more information check out the Recon Village archived talks from Defcon. Also, keep in touch by signing up the mailing list below. New additions will be added to this page and dnsdumpster.com in the near future.